Understanding Permission Types
Microsoft uses two types of OAuth permissions:| Type | Who Acts | When Used |
|---|---|---|
| Delegated | User on their own behalf | User is signed in. Actions happen as that user with their access rights. |
| Application | App on behalf of org | No user signed in. App has its own access (e.g., background jobs). |
Langdock uses delegated permissions. When you connect a Microsoft integration, Langdock acts on your behalf with your existing access rights—it cannot access data you don’t already have access to.
Granting Admin Consent
A Microsoft admin must grant tenant-wide consent before users can connect Microsoft integrations.Prerequisite: A user or admin must have attempted to connect an integration at least once. This triggers the creation of the Langdock Service Principal in your tenant.
Open Microsoft Entra
Sign in to the Microsoft Entra admin center as a Cloud Application Administrator or Global Administrator.
Find Langdock
Go to Identity → Applications → Enterprise applications → All applications and select Langdock.
Grant Consent
Under Security, select Permissions, then click Grant admin consent for [Your Organization].
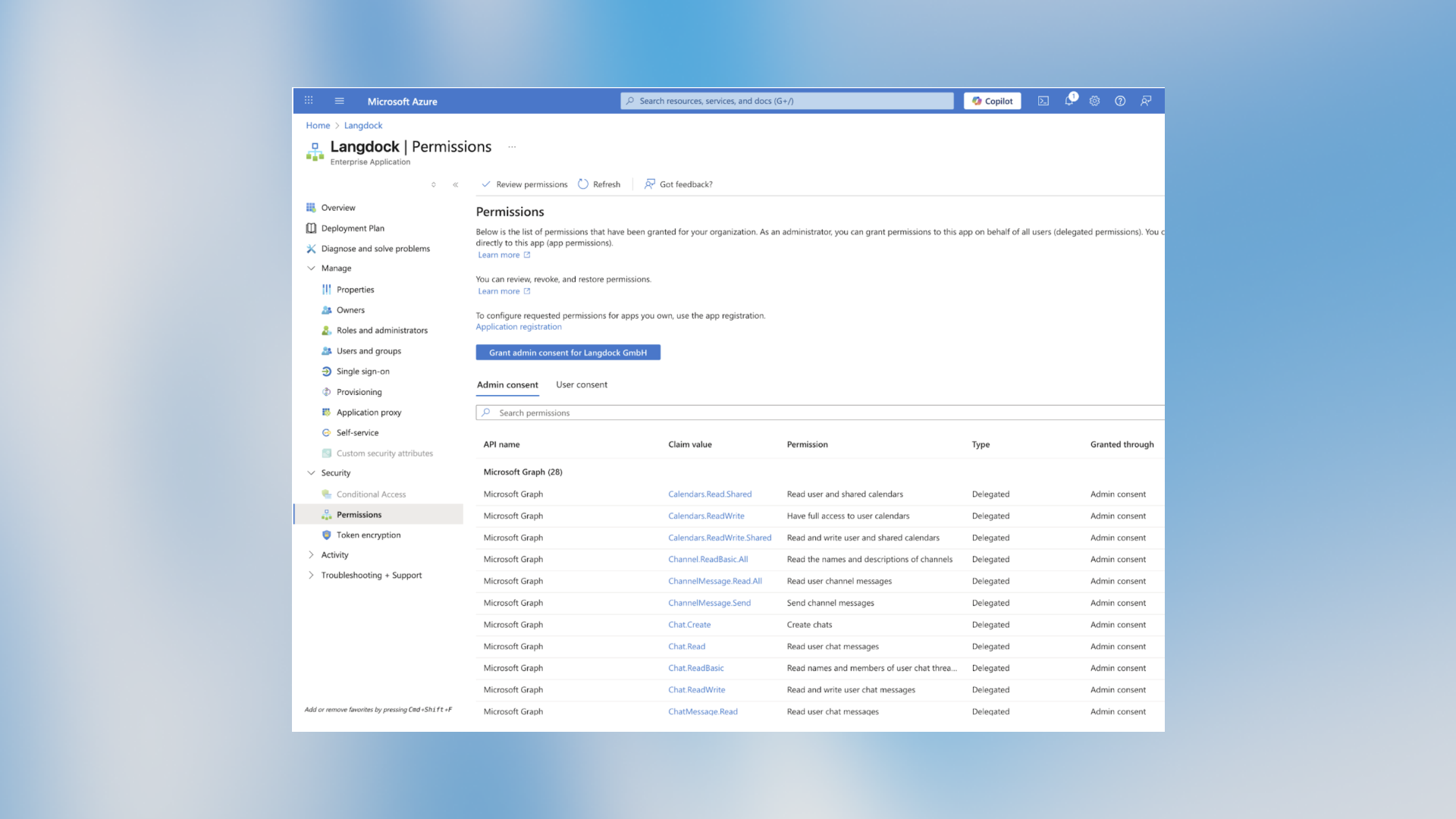
Reviewing Granted Permissions
After granting consent, you can review all permissions in Microsoft Entra:- Go to Identity → Applications → Enterprise applications → Langdock
- Under Security, click Permissions
Viewing Required Permissions per Integration
Each Microsoft integration requires specific permissions (scopes). To see what a particular integration needs:- In Langdock, go to Settings → Integrations
- Click on the Microsoft integration (e.g., Outlook Calendar)
- Click Configure your own in the OAuth dropdown
- View the Required Scopes section
Common Permissions
| Permission | What It Allows |
|---|---|
Calendars.ReadWrite | Read and create calendar events |
Mail.ReadWrite | Read and send emails |
Files.ReadWrite.All | Access OneDrive/SharePoint files |
User.Read | Read your basic profile |
offline_access | Maintain access without re-login |
Customizing Permissions
If your organization requires different scopes than Langdock’s defaults, you can configure your own OAuth client.Configure Custom OAuth Client
Set up your own OAuth application to control exactly which scopes are requested.